Introducing Bio-Auth
Simple. Secure. Authentication.
Eliminate Passwords Now

#LetsEliminateThePassword.
Electronic Medical Records—the lifeblood of any Healthcare Organization—are potentially placed at risk every time users authenticate. Whether a company’s employees use sanctioned password requirements or look to bypass protocol with unsanctioned shared passwords, the inadequate security and compliance standards of these methods is a serious liability.
Bio-Auth solves this problem with an enterprise-grade layered authentication platform which meet compliance requirements, that gives users the ability to easily authenticate without using passwords, while providing IT with, comprehensive controls, auditing and access tracking capabilities.

Passwords are a major problem, one that can have serious consequences for Healthcare organizations, yet it’s a problem that’s easy to mitigate by implementing Bio-Auth which incorporates multi-factor and layered authentication.
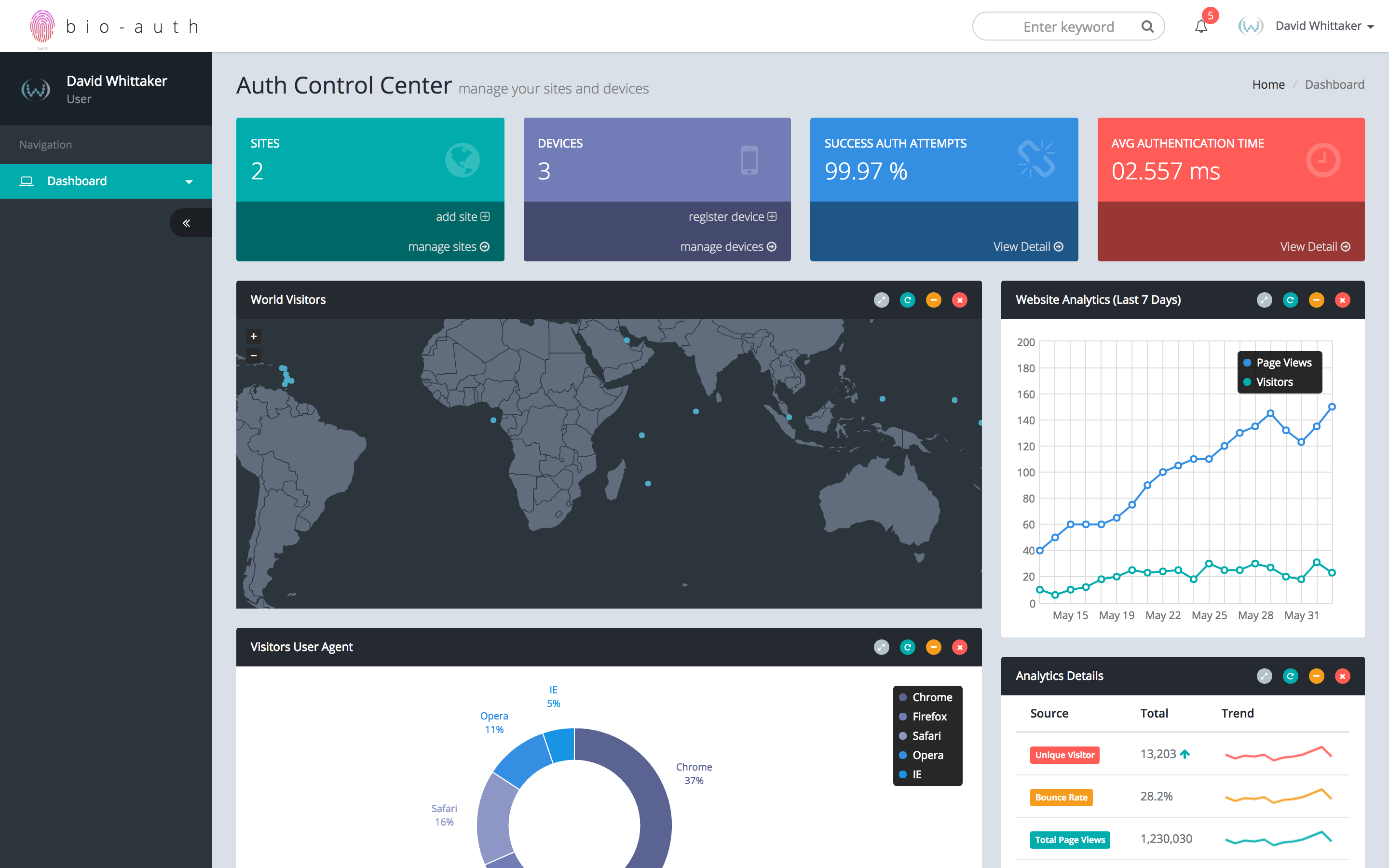

Bio-Auth integrates seamlessly with existing infrastructure and applications while providing IT with granular authentication control capabilities.
Enterprises can quickly get started using Active Directory/LDAP or SAML 2.0 integration to enable SSO, while SAML provisioning support eases the work of IT by automating the user account setup process. In managing accounts, Bio-Auth provides administrative flexibility by allowing IT admins to set global controls, use new or existing role-based groups or apply policies at the individual account level.
On the Bio-Auth 2.0 platform authentication exists in many forms
and in layered combinations
HeartID can validate a user’s identity based on ECG sampling, and subsequently authenticate them in a secure and continuous manner.
Gait refers to the style of walking of an individual which is an attractive modality for identification and authentication distance.
Apply a face recognition system capable of identifying or verifying a person from a digital image or a video frame from a video source.
Internet of things devices can be used in sequential processing of authentication enhancing identification.
Use precise Geo-Location coordinates or ranging in your layered authentication platform.
Utilize indoor access based authentication on Nearfield Communications and Beacon Technology.
For any sales related questions, more information, or schedule a demonstration
please send us a note we would love to talk to you.